Managing Risks and Opportunities for ISO 27001 Compliance
Implementing an information security management system (ISMS) compliant with ISO 27001 can seem like a daunting task for many organisations. However, taking a systematic approach and focusing on risk management, as outlined in Clause 6.1 of the standard, can simplify the process.
In this post, we’ll explore how to address risks and opportunities as part of planning your ISO 27001 ISMS. Implementing these steps can help ensure your ISMS meets requirements and achieves continual improvement.
Overview of Clause 6.1
Clause 6.1 covers explicitly “Actions to address risks and opportunities” as part of the overall planning process for an ISO 27001-compliant ISMS.
Here are the key points:
- Consider the context of the organisation (clause 4.1) and interested parties (clause 4.2)
- Identify risks and opportunities related to achieving intended outcomes and preventing undesired effects
- Plan actions to address these risks and opportunities
- Integrate actions into ISMS processes
- Evaluate the effectiveness of actions
Proper risk management ensures that your ISMS is appropriate for your organisation’s context and that you prevent or reduce any undesired incidents. It’s a continuous process that enables continual improvement.
Conducting an Information Security Risk Assessment
An essential requirement under clause 6.1.2 is to define and apply an information security risk assessment process. This involves:
- Establishing risk assessment criteria
- For example, definitions of risk impact and likelihood.
- Ensuring repeatable and consistent assessments
- Using a defined methodology each time.
- Identifying relevant risks
- Related to confidentiality, integrity, and availability of information.
- Analysing potential consequences and likelihoods
- Evaluating how severe and probable risks are.
- Comparing analysis to criteria
- Prioritising higher risks for treatment.
- Documenting the process
- Retaining risk assessment records and results.
Following a structured methodology using metrics like risk matrices ensures objective, consistent risk analysis. It also provides the necessary inputs for risk treatment.
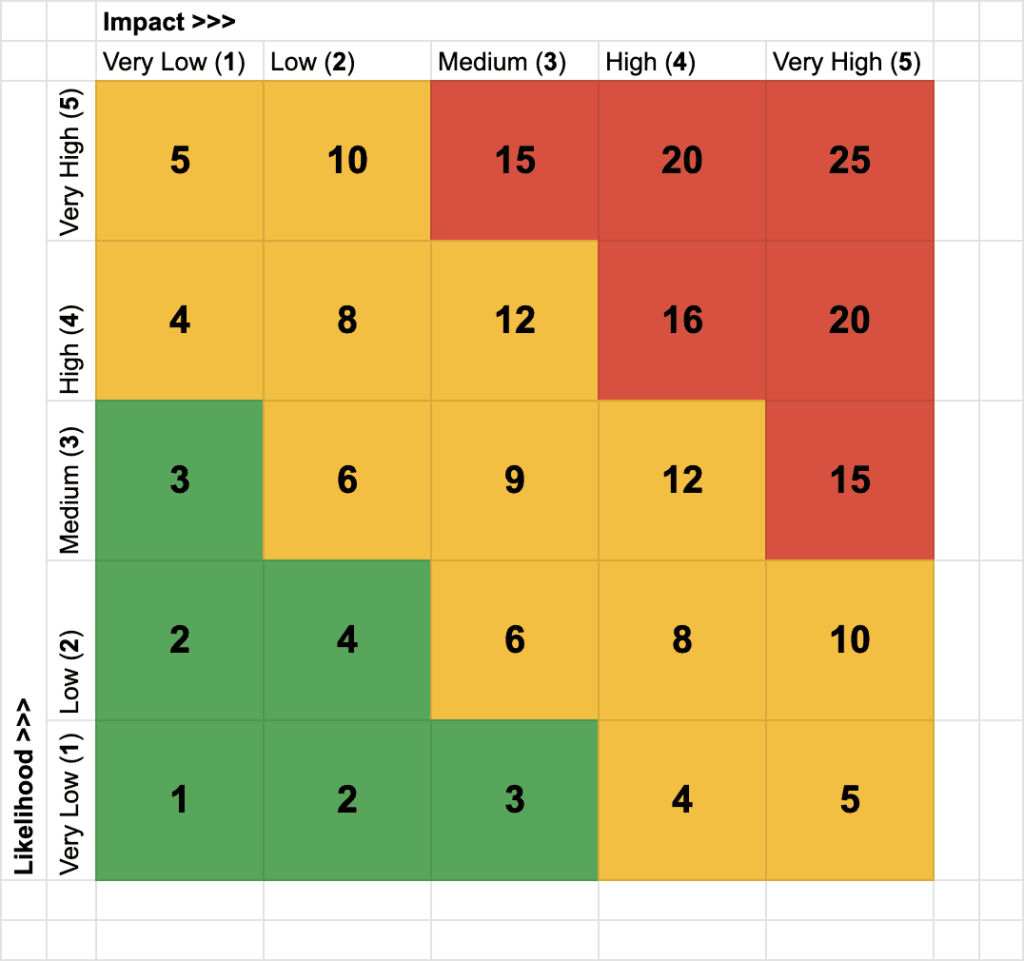
I like using a simple 1-5 scale to rate impact and likelihood. This allows quick prioritisation of higher risk items in the 5 x 5 matrix.
Treating Information Security Risks
Clause 6.1.3 covers information security risk treatment. The key steps include:
- Selecting appropriate options to address risks
- For example, implementing controls to reduce risk.
- Determining necessary controls
- Identifying controls that help mitigate unacceptable risks.
- Comparing to Annex A of ISO 27001
- Ensuring no necessary controls are missed.
- Producing a Statement of Applicability
- Documenting controls chosen and justification.
- Formulating a treatment plan
- Defining an action plan for implementing controls.
- Obtaining approval from risk owners
- Getting buy-in on residual risks.
The risk treatment process takes the risk assessment outputs and turns them into a concrete set of actions. The treatment plan summarises who is responsible for implementing controls and by when.
Remember to involve risk owners in finalising the treatment plan. This ensures they agree with residual risk levels where risks are partly mitigated rather than entirely eliminated.
Tips for Effective Risk Management
Here are some tips for your ISO 27001 risk management process:
✅ Involve the right people – Include a cross-section of leadership, IT, legal, HR and other business units in risk assessments.
✅ Leverage available resources – Re-use risk identification from other projects to kickstart assessment.
✅ Keep it simple – Start with qualitative ratings before complex quantitative models.
✅ Focus on priority risks – Not all risks can be addressed immediately. Focus on critical ones first.
✅ Regularly review and update – Schedule reviews to keep risks current and treatments effective.
Benefits of Risk-Based Thinking
Taking a risk-based approach when planning your ISO 27001 ISMS implementation brings many advantages:
- Prioritises controls and actions – This lets you focus resources on critical risks.
- Demonstrates due diligence – Evidence of prudent risk management.
- Encourages proactive management – Addresses risks before incidents happen.
- Promotes continuous improvement – By regularly reviewing risks.
- Optimises spending – Targets controls to highest priority risks and opportunities.
By proactively identifying and treating information security risks, you can build an adaptive ISMS focused on preventing the most critical incidents. This ultimately saves time and money compared to reacting to events after they occur.
Achieving ISO 27001 Certification
While ISO 27001 has specific requirements around risk management, the overall approach is flexible. Organisations can tailor their risk assessment and treatment methodology based on their own context and risk appetite.
Here are some tips for completing Clause 6.1 activities while progressing towards certification:
- Collaborate with an experienced consultant as a coach
- Start risk management early when implementing your ISMS
- Integrate risk management into your processes
- Use simple qualitative analysis before quantitative models
- Align to your organisation’s existing risk practices
- Consider risks at least annually or after major changes
- Maintain risk assessment and treatment records
With the proper focus on risk management, organisations of any size and sector can implement ISO 27001 successfully. And don’t worry – although risk-based thinking is important, with the right guidance, it doesn’t need to be a complex endeavour!
Key Takeaways
- Clause 6.1 covers how to address information security risks and opportunities when planning your ISO 27001 ISMS.
- A structured risk assessment methodology is key to consistent, repeatable analysis.
- Risk treatment involves selecting controls and formulating an action plan.
- Effective risk management ultimately saves time and money.
- Flexible risk-based thinking allows ISO 27001 alignment for diverse organisations.
Summary: ISO 27001 Risk Management Essentials
- Clause 6.1 focuses on risk and opportunity management when planning an ISO 27001 ISMS.
- Key activities include risk identification, analysis, evaluation and treatment.
- Following a defined risk assessment methodology ensures repeatable results.
- Risk treatment involves selecting controls and defining an action plan.
- Involving stakeholders, keeping it simple, and having regular reviews help effectiveness.
- The risk-based approach in ISO 27001 allows tailored implementation.
- With the right guidance, organisations of any size can manage risks for ISO 27001.
FAQ
Q: What is the purpose of risk management in ISO 27001?
A: The purpose is to identify information security risks and opportunities to determine which ones need treatment by implementing controls. This ensures that the ISMS achieves intended outcomes and prevents undesired incidents.
Q: How often should risk assessments be repeated?
A: Risk assessments should be conducted at least annually and also after any major changes to the organisation or technology environment. More frequent reviews may be warranted for higher priority risks.
Q: Can we outsource risk assessment to a consultant?
A: Yes, you can outsource risk assessments to an experienced ISO 27001 consultant. They can help facilitate workshops, provide advice on risk analysis, and document the risk treatment plan. However, responsibility remains with your organisation’s leadership team.
Q: What if risk owners disagree with the treatment plan?
A: If risk owners are uncomfortable with residual risk levels, further analysis may be required to identify additional controls to implement. Their sign-off is important, so additional workshops and communication may be needed to get agreement.
Q: Which risks should be our priority for treatment?
A: The highest priority risks are those with both a higher likelihood of occurring and a higher impact if they do occur. The risk assessment process will allow you to identify and focus on these risks. Cost vs reward is also a consideration in selecting how to treat risks.